This Week
When password strength meters disagree (and what to do instead). Also: when to say yes to UAC.
From a Starbucks, outside of St. Louis
I'll be home by the time you read this, but I'm sitting in a Starbucks (of course) outside of St. Louis, MO, not far from a very large gathering of Pembroke Welsh Corgis. It's been a blast. :-)
•
Why Do Password-strength Meters Give Different Results?

From a purely algorithmic, or mathematical, perspective, cracking passwords is a fascinating problem.
From a user's perspective, however, it's not that fascinating at all. In fact, it's downright frustrating. One of the best examples of that frustration is the scenario you outline: one sites' “great” password might be considered horribly insecure by another.
What's a user to do?
My recommendation? Create strong passwords that don't need a password-strength meter at all.
Different schools of thought
Ask different IT pros about the best way to generate a strong password, and you'll get about as many different answers as people you ask. There's no agreement on what makes a password-creation technique both safe and easy enough to use.
Different people prioritize:
|
It turns out the same is true for password cracking and password-strength meters: they all have different priorities.
Priorities when cracking
A hacker trying to crack a password database wants to get the highest return on his investment in time and technology. That means cracking passwords that are easily crackable first, and then maybe moving on to others later.
As pointed out by Steve Gibson (on his excellent passwords haystack page):
Once an exhaustive password search begins,
the most important factor is password length!
Meaning that if a password search is simply running through all possible passwords — a so-called “brute force” attack — then the longer your password, the less likely it is to be discovered.
Many password-strength meters prioritize this concept or rely on it exclusively. The first strength meter you used probably falls into this bucket. A 20-character password — any 20-character password — would take centuries to discover using brute force methods. On the other hand, an eight-character password — any eight-character password — is easy to crack these days.
Of course, there are other methods.
Alternate approaches to cracking
Thanks to database breaches in the last several years, a lot of information about real passwords used by actual people has become available.
I'm sure you've seen the “top X worst password” lists that appear every year or so. That's the result of analyzing those databases. It's also just the tip of the information iceberg.
Researchers analyze that information to see how people try to make their passwords more obscure. Then they transform what they find into computer algorithms, which can then be used in password-strength meters.
For example: the research shows that simply replacing some letters in your favorite password with similarly formed letters doesn't add much security to an otherwise bad password. “Password” is a bad password, but “P4ssw0rd” is no better. If you jump around with capitalization, or maybe add a special character or two to the end, you're still no better off. “Password” is still bad, and “pAsSWoRd22” really doesn't help much at all.
Trying to improve a password by making it harder to guess is almost bound to fail. Not because hackers will guess it, but because they've already seen your method being used in massive collections of stolen passwords.
Remember, hackers are researchers too. If there's something even a few people do to obfuscate their passwords, hackers probably know about it.
If it's ever been used…
One more approach to password cracking is a different kind of “brute force”: just try all known passwords.
As we've seen, researchers (and hackers doing their own research) often use huge databases of hacked passwords — passwords that people actually use.
Sometimes there's no “research” involved: they just try them all.
If your password has been used even once, anywhere that has suffered a breach, it may be in one of these massive databases. It doesn't matter how complex or secure it may be. It could still be part of the hacker's future attempts on other services.
Alternate approaches to strength meters
With all the different ways hackers can figure out passwords, it's really no surprise that strength meters might not take every single approach into consideration. The result is that, depending on your proposed password and the approaches that a particular strength meter might look for, the same password may pass as “secure” on some meters, or fail as “easy to crack” on others.
It's frustrating. I get it.
And that's also why I can't point you to a single password-strength meter I would consider “the best”, because I don't know what approaches they take into account, and what approaches they overlook.
If you must use a strength meter, use more than one. If any report your password as easy to crack, believe it and choose a different password.
But we can also learn something about passwords from everything we've discovered so far.
Creating better passwords — no meter required
There are two characteristics that put passwords at risk:
- Any kind of pattern. Be it a pattern you see, or a technique you use to make passwords obscure, if there are repeatable steps to make it work, then those steps (or algorithm) are a pattern that can be discovered.
- Any kind of re-use. No matter how strong it is, if your password is discovered in one database, it could become part of the hacker's arsenal of passwords to try elsewhere.1
The solution is simple:
- Use completely random passwords, long enough to make brute force attempts unfeasible.
- Never reuse passwords. Period.
Yes, it'll require that you use a password vault, since those passwords fail the “memorable” test. As I've said many times, using password-management software is safer than not using it, specifically because it allows you to use these super-strong random passwords. It'll even help you create them.
What I do
I rarely pay attention to password-strength meters, and I certainly don't go looking for them.
Instead, I let LastPass generate 20-character completely random passwords for me. Here's an example: z9UBwPn7kDUMCe4SKjEh.
It passes both of your password-strength meters with flying colors.
For bonus points, consider adding two-factor authentication to your accounts whenever possible. That way, even if your password is discovered, hackers encounter an additional, nearly insurmountable barrier protecting your account.
Related Links & Comments: Why Do Password-strength Meters Give Different Results?
https://askleo.com/30068
•
The Ask Leo! Guide to Online Privacy
|
There's no avoiding the issue: privacy issues are scary, complex, and even somewhat mystifying. The Ask Leo! Guide to Online Privacy tackles these topics in terms you can understand. The Ask Leo! Guide to Online Privacy will help you understand what's at risk, what steps to take, and what to do when you're not sure. |

|
•
When Is It Safe to Say "Yes" to User Account Control (UAC) Notifications?
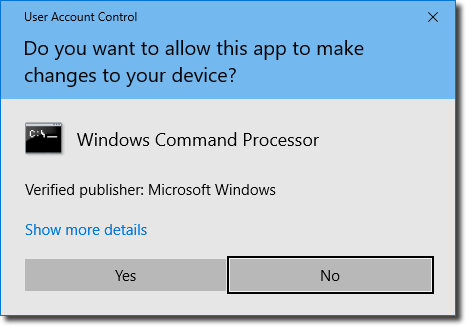
What you're seeing is Windows' “User Account Control”, or UAC. The basic premise is that before software does anything that could potentially install malicious software or otherwise harm your computer, the system asks you first.
The knee-jerk reaction is, “If you're not sure, say no”. The problem is, there are most definitely times and situations where “Yes” is the correct answer.
There are some things you can keep in mind that will let you be a little more sure a little more often, and as a result, allow you to make a more informed decision.
Continue Reading: When Is It Safe to Say "Yes" to User Account Control (UAC) Notifications?
https://askleo.com/4207
•
The Ask Leo! Tip of the Day
A feature exclusively available to Ask Leo! Patrons Bronze level & above.
- Tip of the Day: Try Caret Browsing
- Tip of the Day: Use More Power!
- Tip of the Day: Don't Believe Everything You Read
- Tip of the Day: Quick Keystroke Formatting in Word and Other Programs
- Tip of the Day: Newer TVs Make Great Computer Displays
- Tip of the Day: Who Owns that Website?
- Tip of the Day: Read the Fine Print with Your Camera
•
More Ask Leo!
Become a Patron
Books -
Business -
Glossary
Facebook -
YouTube -
More..
•
Leo's Other Projects....
HeroicStories Since 1999, HeroicStories brings diverse, international voices to the world ' reminding us that people are good, that individuals and individual action matter. Stories - new and old - are published twice a week.Not All News Is Bad - Each day I look for one story in the current news of the day with a positive bent. Just one. And I share it.
leo.notenboom.org - My personal blog. Part writing exercise, part ranting platform, it's where I write about anything and everything and nothing at all.
•
Help Ask Leo! Just forward this message, in its entirety (but without your unsubscribe link below) to your friends. Or, just point them at https://newsletter.askleo.com for their own FREE subscription!
Newsletter contents Copyright © 2017,
Leo A. Notenboom & Puget Sound Software, LLC.
Ask Leo! is a registered trademark ® of Puget Sound Software,
LLC
