This Week's Newsletter
Spectre and Meltdown. I originally wasn't planning on writing about them, since there's already been so much press, and like so many of these issues in a few weeks it'll all have blown over. However because there's been so much press it's stirring up a lot of FUD (Fear, Uncertainty, and Doubt) around the hardware issues they represent. So, I caved, and What Do I Need to Do About Spectre and Meltdown? covers what you should do. As I dove into the very technical details (it's incredibly complex), I found myself fascinated and even managed to come up with an analogy that might help you understand just what the heck these two beasties are.
In other news it's time for the annual look-back, CPUs doing nothing while your system is slow, and the probability of getting hacked after you pull the plug.
•
Can My Computer Be Hacked If It's Turned Off?

It's a very unlikely scenario that could allow a turned-off computer to be hacked. I'll describe it and show you how to prevent it.
Fifty percent say no?
Welcome to the world of technology, where there are very rarely black-and-white answers.
One of my most common phrases (that I get kidded about by my assistants) is: “It depends.”
There are rarely yes-or-no answers to technological questions. The real answer is usually nuanced and depends on many factors.
This happens to be one of them.
Hacking a turned-off computer
The good news is that in general, the answer is “No.”
Your PC is off; it's not doing anything. Unless you've taken extra steps described below, the PC will not be able to be restarted and hacked from outside if it's turned off, even if you leave it connected to the internet and to power.
The exception to the rule is a feature that, when enabled, allows a PC to be remotely turned on and booted. In short, the network adapter for the computer is not turned off completely, but instead monitors for specific instructions that tell it to wake up. When those instructions are received, power is restored to the computer and it boots.
In such a scenario, if the PC has been configured to respond to the remote requests, then the PC could be turned on and booted remotely.
At that point, if the PC did not have appropriate security software installed (say it was not behind a firewall and it did not have anti-malware tools), then it is conceivable the PC could be hacked remotely, even though it was powered off.
One caveat: standby
It's not uncommon for a laptop to be placed into standby mode only to wake up on its own a while later. The exact reasons this happens vary — I can't give you a simple explanation.
There is a simple work around, though: if you find your laptop waking up on its own, and that concerns you, don't use standby.
If it works for you, that's great, but I generally avoid standby for a variety of reasons, including this one.
Allowing remote access
Hacking a turned-off machine is extremely unlikely.
A lot of things have to line up for it to happen. You have to have this remote power-on ability (Wake on LAN) turned on in the network settings, and most computers do not. In most cases, it's a setting in the UEFI or BIOS you have to turn on yourself. If you haven't turned it on, then it's probably not on.
The PC also has to be fundamentally insecure. In other words, it has to be vulnerable to be being hacked when it's running. That's something you can control by putting appropriate security measures into place.
So, as I said, it's possible.
It's just extremely unlikely.
Related Links & Comments: Can My Computer Be Hacked If It's Turned Off?
https://askleo.com/5253
•
The Ask Leo! Tip Of The Day!
An emailed tip six days a week to help you use your computer, and your technology, more effectively and with more confidence. Includes online access to all previous tips, as well as Ad-Free Ask Leo! There's something for everyone, from beginner to the experienced computer user. By popular demand: now available as a monthly or annual subscription. Support Ask Leo! by purchasing a subscription to The Ask Leo! Tip Of The Day. Thanks! -Leo |
 |
•
2017's Most Popular Articles

It's that time of the year again: the time for lists!
As I do each year, I'll look back on the most popular articles based on both the number of times the article was viewed and the number of comments posted by viewers.
Continue Reading: 2017's Most Popular Articles
https://askleo.com/32505
•
Why is My System Slow If the CPU Is Mostly Idle?
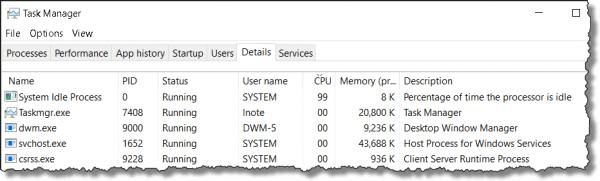
I get a lot of pushback on that older article from people who are absolutely convinced the System Idle Process is somehow evil and must be eradicated simply because their computer is slow and “System Idle Process” is at the top of the CPU usage list.
They are wrong.
System idle is benign. The CPU has to do something 100% of the time. When it has nothing to do for you or the system, it's assigned the idle task to while away the time. It's the CPU equivalent of twiddling your thumbs, waiting for something to do.
So why is your system slow as molasses?
Well, I'll give you one hint: the CPU is not the only thing in your computer that affects its speed.
Continue Reading: Why is My System Slow If the CPU Is Mostly Idle?
https://askleo.com/4338
•
What Do I Need to Do About Spectre and Meltdown?

Two newly discovered vulnerabilities have been getting a lot of press recently. Much of it has been quite sensationalistic, due to the nature of the underlying issues.
The flaws are in hardware design — specifically the CPU — and not just one CPU, but apparently a wide variety of CPUs — meaning that just about any computer or device using the most popular CPUs of the last couple of decades is probably vulnerable to the issue.
So, to answer everyone's first question: yes, your computer or mobile device is likely affected.
The next question is, what to do about it?
Step one: don't panic.
Continue Reading: What Do I Need to Do About Spectre and Meltdown?
https://askleo.com/32964
•
The Ask Leo! Tip of the Day
A feature exclusively available to Ask Leo! Patrons Bronze level & above.
- Tip of the Day: Watch Your CPU Usage for Malware
- Tip of the Day: Restore Trash
- Tip of the Day: Pin Browser Tabs for Quick Access
- Tip of the Day: Force a Complete Shutdown in Windows 10
- Tip of the Day: Get Even More Info From Windows 10 Task Manager
- Tip of the Day: Access Device Manager Quickly
- Tip of the Day: Pay Attention to the URL
•
More Ask Leo!
Become a Patron
Books -
Business -
Glossary
Facebook -
YouTube -
More..
•
Leo's Other Projects....
HeroicStories Since 1999, HeroicStories brings diverse, international voices to the world ' reminding us that people are good, that individuals and individual action matter. Stories - new and old - are published twice a week.Not All News Is Bad - Each day I look for one story in the current news of the day with a positive bent. Just one. And I share it.
leo.notenboom.org - My personal blog. Part writing exercise, part ranting platform, it's where I write about anything and everything and nothing at all.
•
Help Ask Leo! Just forward this message, in its entirety (but without your unsubscribe link below) to your friends. Or, just point them at https://newsletter.askleo.com for their own FREE subscription!
Newsletter contents Copyright © 2018,
Leo A. Notenboom & Puget Sound Software, LLC.
Ask Leo! is a registered trademark ® of Puget Sound Software,
LLC
